OpenText fortify SAST stage in CICD pipeline
- admin
- Devsecops
- February 9, 2024
- 6 minutes

Fortify is a powerful software security scanning tool designed to identify and address vulnerabilities in software applications. Fortify employs static code analysis techniques to analyze source code, bytecode, or binary code for security weaknesses. The primary goal of Fortify is to enhance the security posture of software by detecting and helping developers remediate potential vulnerabilities early in the development lifecycle.
Integrating Fortify into GitLab CI/CD entails incorporating Fortify scans into the CI/CD pipeline, and for this explanation, we’ll focus on leveraging Docker as the execution environment within GitLab.
The architecture of Fortify scanning process
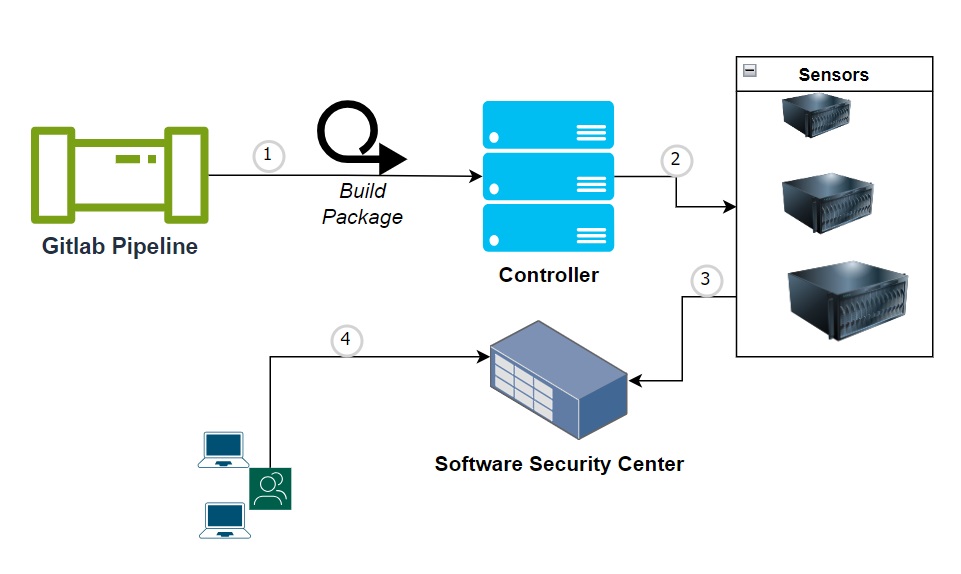
ScanCentral SAST Controller: It serves as a centralized management and orchestration platform for Static Application Security Testing (SAST) activities across an organization. The controller streamlines the scanning process by centrally managing scan requests, distributing workloads to multiple scanning engines, and aggregating scan results.
ScanCentral SAST client: It provides developers and security teams with an interface to interact with the ScanCentral SAST Controller. Through the client, users can initiate and manage Static Application Security Testing (SAST) scans, review scan results, and collaborate on addressing identified vulnerabilities. The client integrates into the development environment, empowering teams to seamlessly incorporate security testing into their software development lifecycle.
ScanCentral SAST sensors: These sensors are integrated into the software development process, providing real-time code analysis and vulnerability detection. By embedding within the development environment, ScanCentral SAST Sensors enable developers to identify and remediate security issues early in the development lifecycle. The sensors support a wide range of programming languages, ensuring comprehensive code coverage and accurate security assessments across diverse application portfolios.
Different modes of scan in Fortify SAST
Full Scan: Fortify always recommends to run the full scan whenever possible. With full scan fortify analyse the source code at its maximum depth. Fortify runs in full scan mode if -quick or -scan-precision are not provided in the scan request.
Quick Scan: The Quick Scan mode offers a swift method to examine the project for critical and high-priority issues. It offers a quick assessment of potential vulnerabilities without the need for a comprehensive and time-consuming scan. Although the scan is faster than the full scan, the result cannot be considered to promote an artifact to the production release. To enable quick scan mode, use the -sargs “-quick” option with -scan option in the static code analyzer. By default, Fortify Software Security Center does not overwrite the results of a full scan with those from FPR files scanned in quick scan mode. However, it is possible to configure a Fortify Software Security Center application version to process FPR files scanned in quick scan mode if desired.
Speed Dial: The speed and the depth of the scan can be adjusted by defining a precision level for the analysis phase. Reducing the precision level can expedite the scan while focusing on identifying a narrower range of vulnerabilities. The results obtained from a scan with lower precision levels are typically deemed insufficient for promoting an artifact to the next stage. As in the quick scan mode, Fortify Software Security Center blocks the upload of analysis result that where created from a scan with a precision level lesser than 4 because it might removes the issues from previous full scans that still exist in the application.
Overview of FCLI tool & fortify-ci-tools docker image
The FCLI is a commandline utility used to interact with various Fortify products, like Fortify on Demand, Software Security Center, Scancentral SAST and DAST. This open-source tool is maintained by the Fortify team, with its source code and documentation available on GitHub.
Fortify offers a docker image containing several tools designed for seamless integration with various Fortify products within a Continuous Integration (CI) pipeline. The below given commands can be executed from the CI pipeline using this image:
- fcli [options]
- scancentral [options]
- FoDUpload [options]
- FortifyVulnerabilityExporter [options]
How to integrate the fortify scanning in Gitlab CI/CD pipeline
In a CI pipeline, each security scanning stages like Software Composition Analysis(SCA), Static Application Security Testing(SAST) contains the jobs Register, Scan and Analyze Result.
In fortify, a user session needs to be created before executing fcli commands. The before_script option in Gitlab CI could be used to execute the session creation commands before executing any other scripts.
Gitlab Variables Configuration
- FCLI_DEFAULT_SAST_CLIENT_AUTH_TOKEN - This token is required to communicate the scan client to the scan central controller.
- FCLI_DEFAULT_SSC_CI_TOKEN - This is a user token used in the CI pipeline to create user session in fortify ssc and execute fcli commands.
- FCLI_DEFAULT_SSC_USER - SSC username
- FCLI_DEFAULT_SSC_PASSWORD - SSC user password
- FCLI_DEFAULT_SSC_URL - Scan central url
- SSC_CONTROLLER_URL - Scan central controller url
- SSC_UPLOAD_TOKEN - This token is used in the scananalzer utility to upload the project content to the scan central
- SSC_SCAN_TEMPLATE - The value “Prioritized High Risk Issue Template” could be used in this variable
Initial Step
FCLI command ssc session is used to login a user and create a session in SSC and the command sc-sast session is used to create a session for SAST scan.
before_script:
- fcli config truststore set -f cacert -p password -t pkcs12
- fcli ssc session login
Register
FCLI command ‘appversion’ is used to create an application version in Fortify scancentral.
To access scan results by different groups within your organization, these groups must be assigned to the project version. While the appversion create command offers an –add-user option for adding users, our test shows that this feature is not operational in the FCLI version.
There is a workaround to assign the user to a specific project version using the REST api endpoint /authEntities/{userId}/projectVersions/action/assign. To execute this endpoint an UnifiedLoginToken is required and it could be created using the FCLI command ** **
before_script:
...
- fcli ssc access-control --expire-in=3m --description=unifiedtoken-${CI_PROJECT_NAME} --store=uaToken UnifiedLoginToken
script:
- fcli ssc appversion create ${APP_NAME}:${APP_VERSION} --issue-template ${SSC_SCAN_TEMPLATE} --auto-required-attrs --skip-if-exists --store appVersion:id
- FORTIFY_TOKEN=$(fcli util variable contents uaToken -o 'expr={restToken}')
- |
curl --header "Authorization: FortifyToken ${FORTIFY_TOKEN}" --header "Content-Type: application/json" --data "{\"projectVersionIds\":[${APP_VERSION_ID}]}" --request POST "${FCLI_DEFAULT_SSC_URL}/authEntities/{FORTIFY_USER_ID}/projectVersions/action/assign"
after_script:
- fcli ssc access-control revoke-token ::uaToken::id
...
Here the variable APP_NAME could be the gitlab repository name (CI_PROJECT_NAME) and the APP_VERSION could be repository branch name(CI_COMMIT_REF_NAME).
Scan
As we encounter challenges in using the fcli command for executing scans in ScanCentral, we opt to use the scancentral command provided within the docker image to initiate scans directly from the CI pipeline.
Before scanning user has to create a SAST session. Add the below command to the before_script to create the SAST session
variables:
SSC_BUILD_OPTS: -bt none
before_script:
... # from initial step
- fcli sc-sast session login
script:
- sed -i "s/client_auth_token=.*/client_auth_token=$FCLI_DEFAULT_SAST_CLIENT_AUTH_TOKEN/" /opt/Fortify/ScanCentral/Core/config/client.properties
- scancentral -url $SSC_CONTROLLER_URL start -upload $SSC_BUILD_OPTS -skipBuild -exclude=".git" -application $APP_NAME -version $APP_VERSION -uptoken $SSC_UPLOAD_TOKEN -email $GITLAB_USER_EMAIL -sargs "-quick"
In the first command, an authentication token is configured within the client.properties file to enable communication between the client and the scan central controller application.
In the second command, the client upload the source code to fortify for scanning. The scan argument "-quick" should be removed when requesting for a full scan. The value of variable GITLAB_USER_EMAIL is transmitted to Fortify to update the user regarding any changes in the status of the scan request.
Result-Analysis
Once the scanning is completed, fetch the result from SSC using the issue count fcli command. This command could fetch the result in json format and write to a file with the given name.
script:
- fcli ssc issue count --appversion="${APP_NAME}:${APP_VERSION}" -o=json --to-file=gl-fortify-sast.json
Final Step
In each stage of fortify source code analysis, it is a best practice to logout from the session.
after_script:
- fcli sc-sast session logout
- fcli ssc session logout
Additional Scripts
In certain scenarios, when initiating a scan from the feature branch, it may not be necessary to retain the application version in Fortify ScanCentral once the scanresult is analyzed. In such instances, you can generate a UnifiedLoginToken and set it in a delete REST API to remove the application version from ScanCentral.
script:
- fcli ssc appversion get ${APP_NAME}:${APP_VERSION} -o expr={id} --store appVersion:id
- APP_VERSION_ID=$(fcli util variable contents appVersion -o 'expr={id}')
- fcli ssc access-control create-token --expire-in=5m --description=delete-token-${APP_VERSION_ID} --store=appToken UnifiedLoginToken
- FORTIFY_TOKEN=$(fcli util variable contents appToken -o 'expr={restToken}')
- |
curl --header "Authorization: FortifyToken ${FORTIFY_TOKEN}" --header "Content-Type: application/json" --request DELETE "${FCLI_DEFAULT_SSC_URL}/api/v1/projectVersions/${APP_VERSION_ID}"
- fcli ssc access-control revoke-token ::appToken::id
Conclusion
As organizations strive for secure and resilient applications, the integration of Fortify SAST in CI/CD emerges as a pivotal step towards enhancing the security posture of your software development lifecycle. Despite the inherent complexity of Fortify SAST scanning, DevOps engineers can seamlessly integrate it into the CI/CD pipeline by leveraging the FCLI tool.
- #Gitlab
- #Fortify
- #Cicd